How To Prevent Fraudulent Carding Attacks On Your WooCommerce Store

Table of Contents
Has this happened to you? You setup a new WooCommerce store. You marketing is working – you are getting customers and they are happy!
But suddenly you start getting some unusual orders. They come in waves and they don’t look quite right. The email addresses don’t look quite right, but the payments are successful so you aren’t sure what to do.
Then it starts: You get a chargeback notice from your payment processor. The transaction has been reported as fraud. Soon afterwards you get more and you realize all of these orders are fraudulent.
You may be a victim of a practice called carding.
Carding is when a scammer obtains a list of stolen of credit cards and uses your website to validate them. Some of the cards have already been compromised and have been disabled. And some of the cards have advanced security – if they try a big purchase, the credit card company may alert the cardholder and they won’t be able to make any purchase.
So the scammer solves the problem by finding a store that has low cost products that they can “purchase” to test whether the card works and also start to build a pattern of online purchases that will allow a larger purchase to go through unnoticed.
How do you stop carding attacks on your WooCommerce store?
Stopping carding attacks on your WooCommerce checkout page is about fundamentally two things:
- We want to stop the attacks!
- We don’t want to impede normal customers.
With that in mind, here are 3 strategies you can use to block or prevent carding attacks.
Best option: Use Cloudflare to protect against bots.
We are huge fans of Cloudflare at CheckoutWC. We use it for all of our sites.
Cloudflare acts as your DNS name server for your website. When configured properly, all traffic to your site goes through their servers on its way to your server.
This has a number of benefits:
- It hides your server’s real IP making direct attacks more difficult.
- They cache your static assets such as CSS, JS, and images and serve them from their servers – basically a powerful CDN.
- They detect and mitigate attack attempts automatically.
For example, here’s a 24 hour snapshot of the threats they stopped on our website:
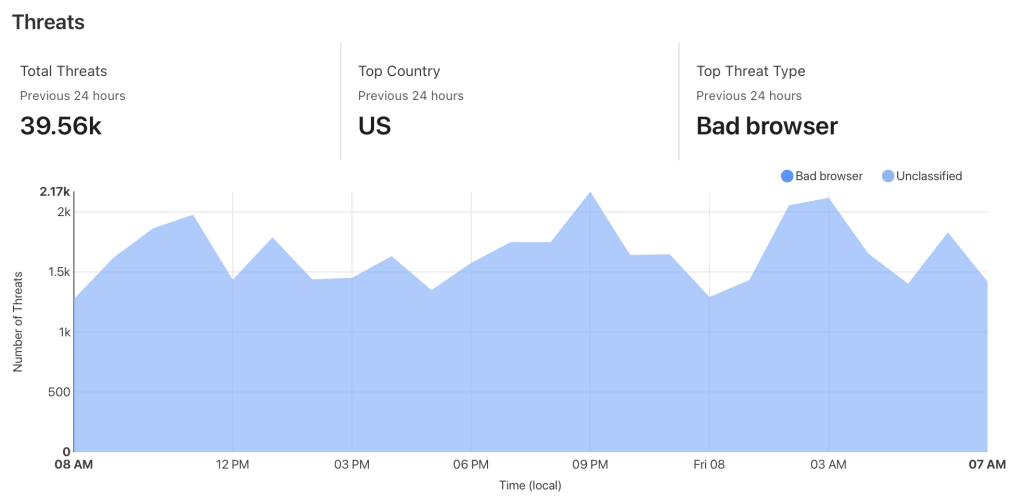
If Cloudflare’s Web Application Firewall (WAF) doesn’t successfully stop your carding attacks, there is another feature you can deploy: Custom WAF Rules
With Custom WAF Rules, you can change the level of security on a particular page. We would recommend starting with a rule that enables a Managed Challenge on your checkout page.
This uses JavaScript to test whether the browser requesting the checkout page is a real person or a bot. If a bot is suspected, it will make the user complete a captcha challenge.
Here’s a screenshot of what this looks like:
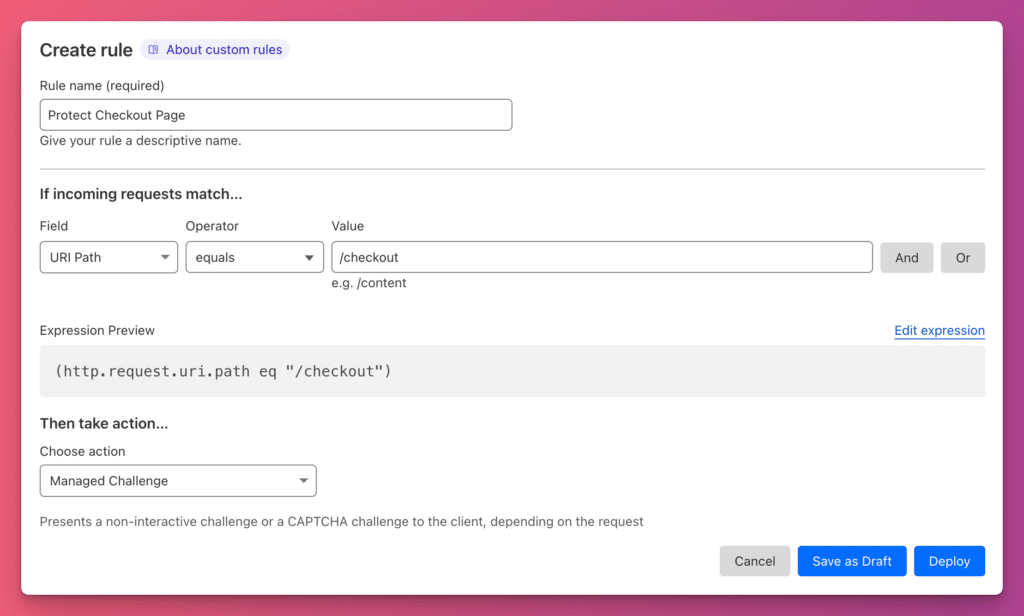
You can add additional settings, such as setting the Security Level to High. However be careful with these rules. Our goal is to avoid impeding real customers and setting your security level too high will result in customers having to complete captchas before they can access the checkout page.
A Managed Challenge should work most of the time.
Next best option: Enable Merchant account protections
Your options here will vary substantially depending on who processes your Credit Card payments. If your merchant services provider doesn’t offer advanced security, it might be time to consider another option.
This is WooCommerce after all – you can use any payment processor you can imagine!
What you are looking for is the ability to configure security thresholds. Here at CheckoutWC, for example, we use Stripe to process credit card payments. Stripe has a feature called Radar which allows us to set our risk tolerance.
Here’s what our Radar setting looks like:
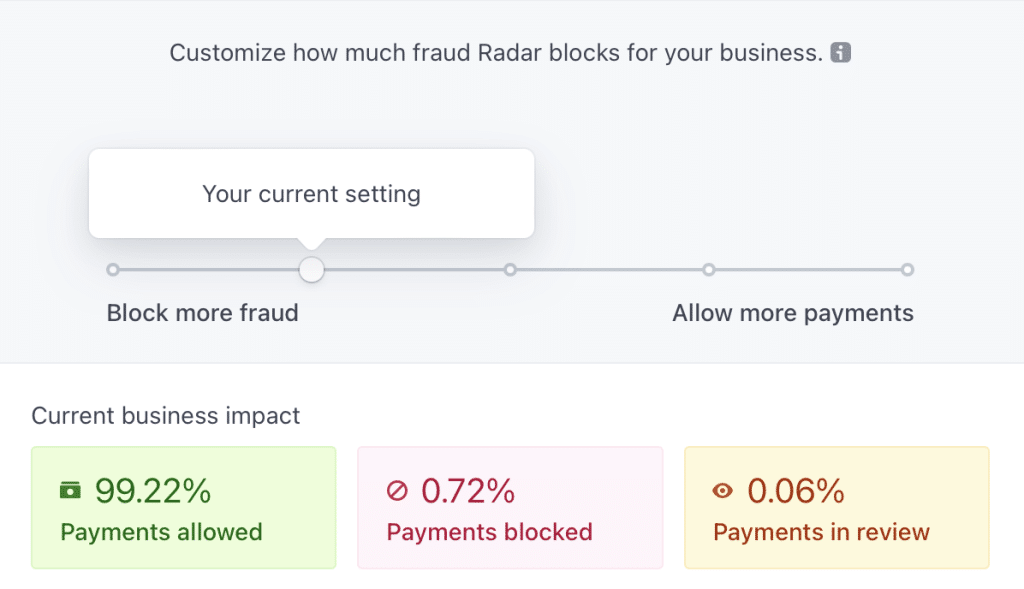
Even if your merchant services provider doesn’t have a fancy machine learning system like Radar, they likely let you configure additional options such as requiring the purchaser to enter a billing zip code and provide the correct CVV for the card.
Additionally they may have options like 3D Secure, which can add additional security.
Less is more here. We don’t want to add friction to the checkout process.
Worst option: Recaptcha for WooCommerce
If you have exhausted your other options and you’re still getting hit, you can try adding a reCaptcha to your checkout page.
But this is really your worst option. It will decrease your conversion rate and you will get fewer legitimate orders.
But the good news is we have fully tested reCaptcha for WooCommerce with CheckoutWC and can confirm it works.
But this probably isn’t the right option.
It isn’t always the bots.
Not every carding attack on your WooCommerce checkout page is coming from bots. Some scammers are manually entering orders. Their goal after all is to soften up the card for a bigger attack later. Staying under the radar is important.
In that case, you may need to review orders before approving them. Sometimes human intuition is more powerful than machine learning.
If you get a lot of suspicious orders, it may be safer to cancel them and refund them before you get hit with chargebacks and financial losses.
How have you stopped carding attacks on your WooCommerce store?
If you have found an effective way to prevent carding, drop us a comment below. We would love to hear your story!
