WooCommerce Security – How to protect your store

This article will cover how to protect your WooCommerce store and customers against the most frequent types of attacks.
Let’s start with the motivation behind the attacks on a website and their consequences for your business:
- Sending spam. It’s not that popular nowadays, but people still do it. Consequently, your hosting or SMTP accounts can be blocked.
- Infecting customers’ devices with malware. This is a more typical case. As a result, you may lose revenue and customers because of antivirus warning messages. Your SEO position and reputation are on the line.
- Testing credit cards, also known as carding. Hackers can use the checkout page on your site to determine if stolen credit card data is valid. It’s the primary reason for spam orders. The payment gateway usually blocks your account if this issue is not resolved quickly. Switching a payment gateway, especially with subscriptions, is not the experience you want to have. This can also result in massive expense – if your store is connected to a 3PL, products could be shipped automatically. And worse, you may end up having to pay for hundreds of even thousands of disputes if you are unable to cancel or refund the transactions before they are disputed.
- Stealing credit card data. This may have the worst consequences for your business. The fines can be as much as $5,000 to $100,000. PCI compliance testing is not enough – you are responsible to keep your customer’s data safe on your site.
- Other motivations, like using your server to attack other sites.
As you may see, there are more than enough reasons to consider your store security seriously.
How the attack is performed
It all starts with getting access to the server. There are a few main ways how sites are hacked:
- Vulnerability in a plugin, theme, or WordPress core. Outdated plugins is a common vulnerability in WordPress sites.
- Using non-genuine (nulled) versions of plugins and themes. A lot of them contain malicious code or a backdoor.
- Stealing the password or cookies from the admin user – this is often performed using an XSS (Cross Site Scripting) attack. Browsers attempt to prevent these types of attacks, but they are still possible, especially if your site has insecure plugins.
- When another site on the same server is hacked. It’s important to not host eCommerce sites on shared hosting. While most hosts have good isolation of sites to prevent one site from accessing another site, it is still a possibility and no hosting service has perfect security.
- By brute-forcing logins and passwords. In this case, a hacker tries to log in under well-known logins and passwords. Using a script, they can try thousands or millions of common username and password combinations. In fact, it’s likely that your WordPress site is currently being attacked this way right now – you just don’t have the tools in place to detect it.
Once the hackers get access, they do the following:
- Upload special scripts to different folders and attach the malicious code to files. Those scripts grant access to files from the web.
- Some of them create additional admin users to ensure continued access.
- Add malicious code doing all those bad things I described before.
How to prevent security breaches
There are a few steps to avoid being hacked:
Update WordPress core, plugins, and themes regularly. To help avoid issues, you should have a staging site where you test updates before deploying them to your live site. Starting with WordPress version 6.2, it is now easy to rollback plugin updates if an update causes a problem.
Use complex passwords and do not open suspicious links, even if they point to your website.
Use a web application firewall (WAF). It blocks suspicious requests and network attacks.
I suggest using Cloudflare WAF. It’s easy to configure, has a decent free plan, and does not generate additional load on the server.
If you can’t use Cloudflare for some reason, consider a security plugin for WordPress like Wordfence, Sucuri, or Solid Security Pro. It makes sense to use them only if you need features like 2FA and a malware scanner in addition to a firewall.
Please note that those plugins are heavy and can cause additional server load. Having them just for the firewall does not make sense.
I prefer Wordfence because it offers a decent free tier, a reasonable malware and file modification scanner, 2FA, and many other features.
Here are some notes about the Wordfence configuration:
3.1. Enable two-factor authentication for administrators and your account. It’s located under the Login Security menu:
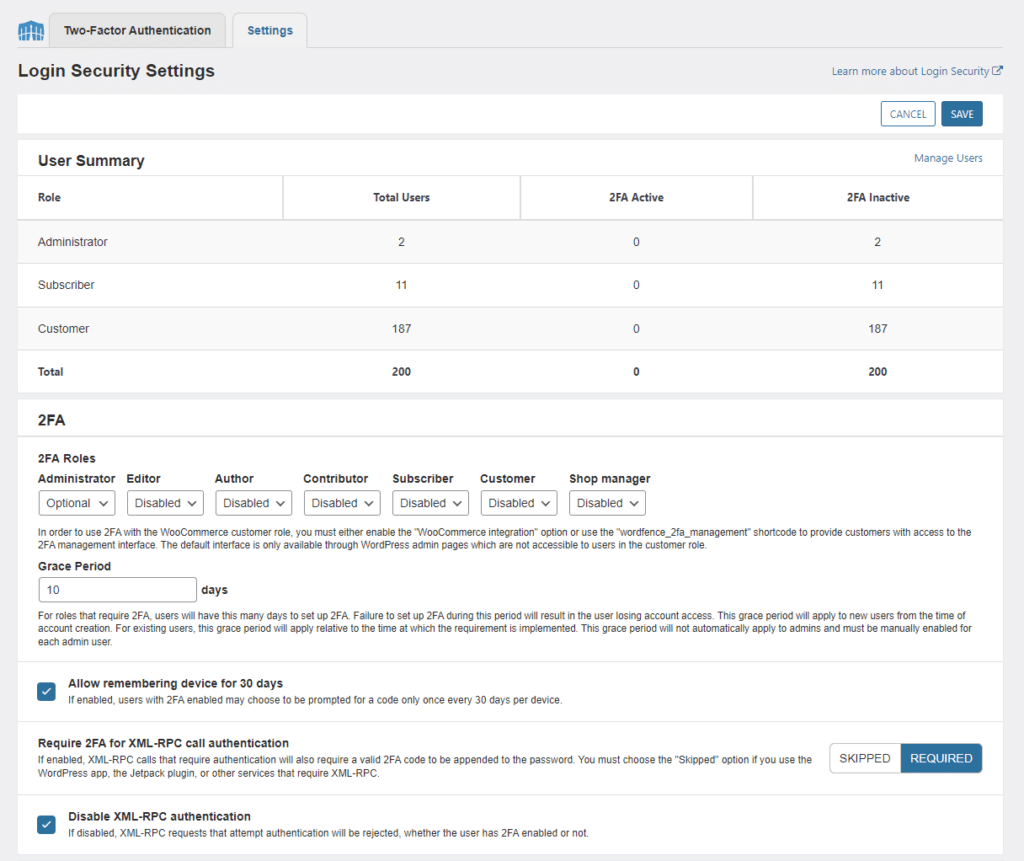
3.2. I recommend turning off the XML-RPC authentification. This is an older, obsolete API for accessing your site that you almost certainly don’t need, but hackers love it.
3.3. I recommend enabling security scans. You can find those settings on the All Options page:
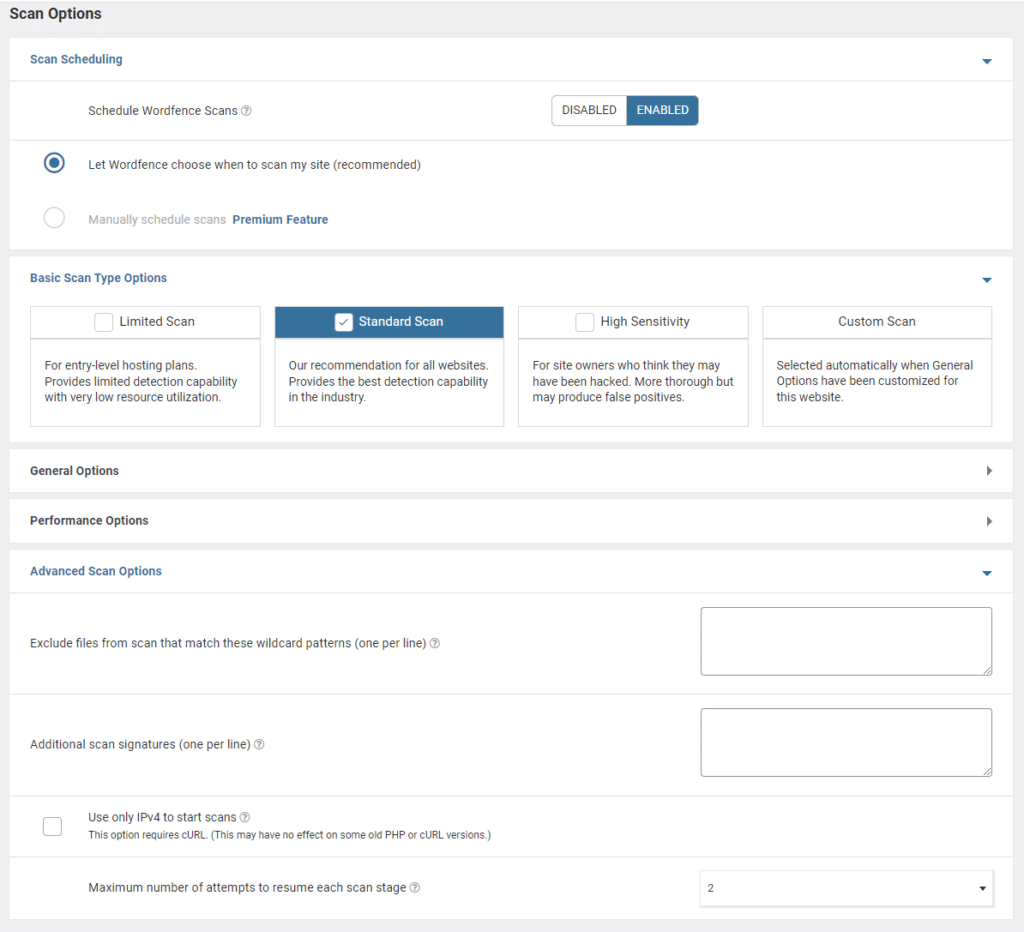
Make sure that the sensitivity is set to Standard Scan or High Sensitivity. Also, check the list of excluded files. Sometimes, hackers add their scripts there!
3.4. Make sure the firewall and brute force protection are enabled:
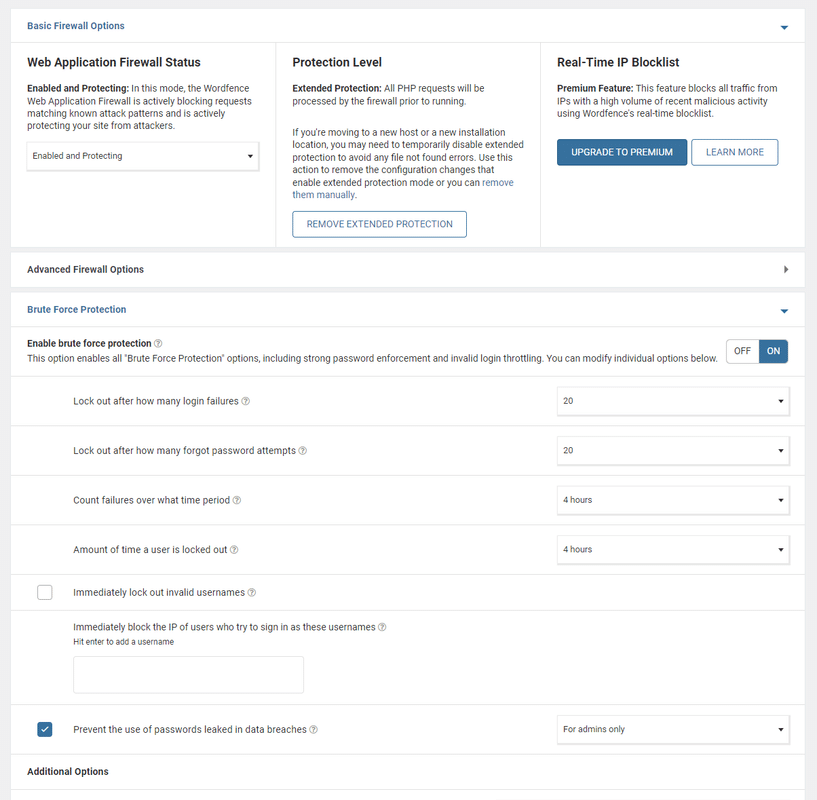
They are beneficial against attempts to find the passwords and logins.
3.5. In some cases, it makes sense to enable rate-limiting:
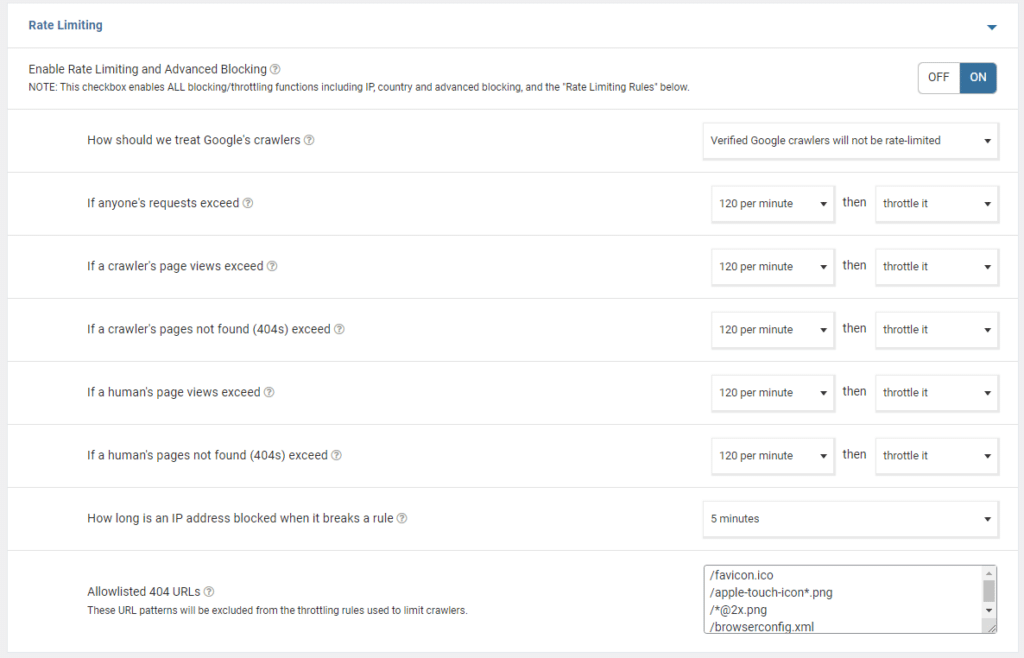
It’s essential when you have a DDoS attack or when your server is experiencing many requests from a few addresses.
Note that Cloudflare WAF offers way better protection against DDoS than any security plugin can provide!
As for the other settings, they are less common.
You can use the invisible reCAPTCHA for checkout and payment pages. It helps prevent credit card testing (carding) attacks and spam orders.
Please note that any captcha implementation can negatively affect your conversion rate. Use reCaptcha only if you have problems with spam orders or see unusual activity in your payment gateway account.
If a full interactive reCAPTCHA is required, I prefer using the reCAPTCHA for WooCommerce plugin. It works smoothly with CheckoutWC.
Setting up reCAPTCHA is fairly straightforward:
4.1. Go to the reCaptcha Admin Console:
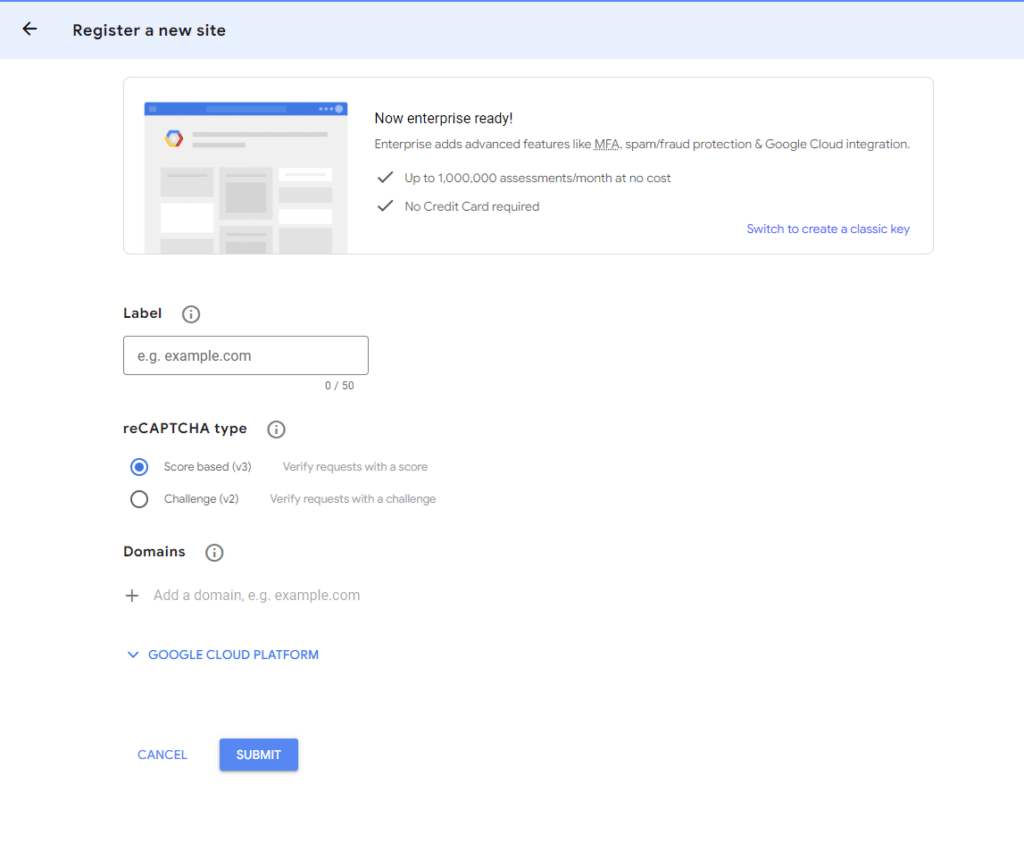
4.2. Specify the label for the key, type (V3 is best for new sites), and domain
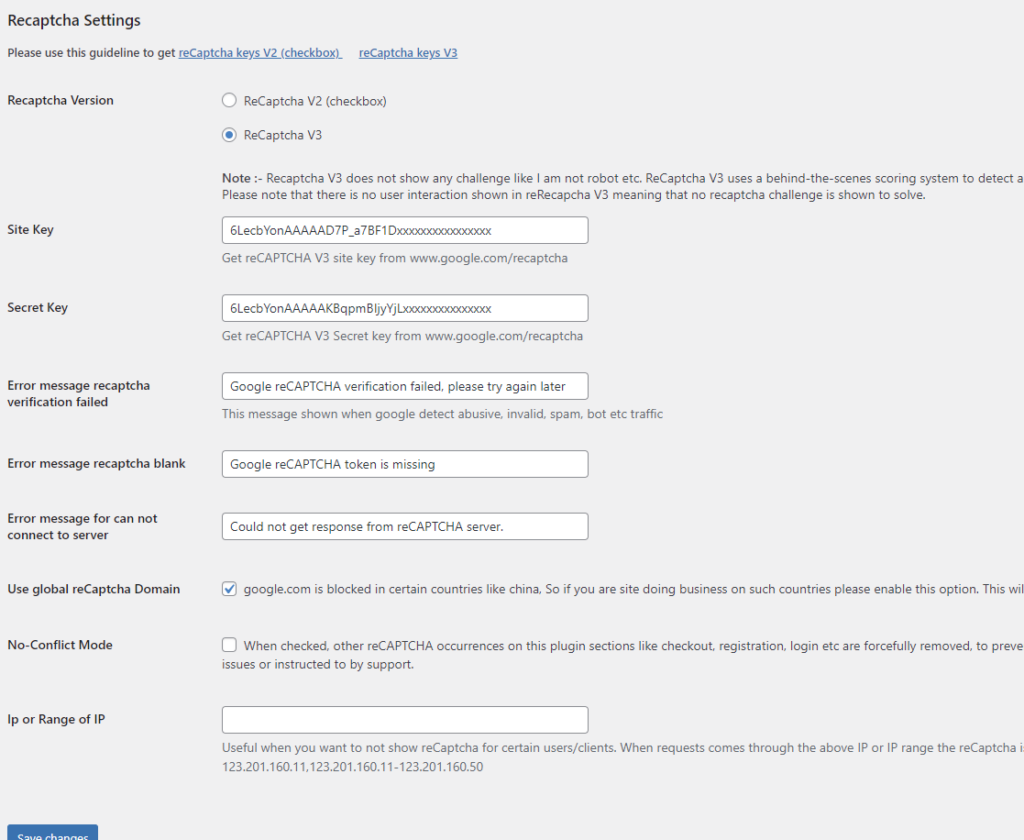
4.3. You will be given a Site Key and Secret Key, which you will enter in the plugin’s settings:
4.4. If you need reCAPTCHA, it makes sense to enable it for the checkout page:
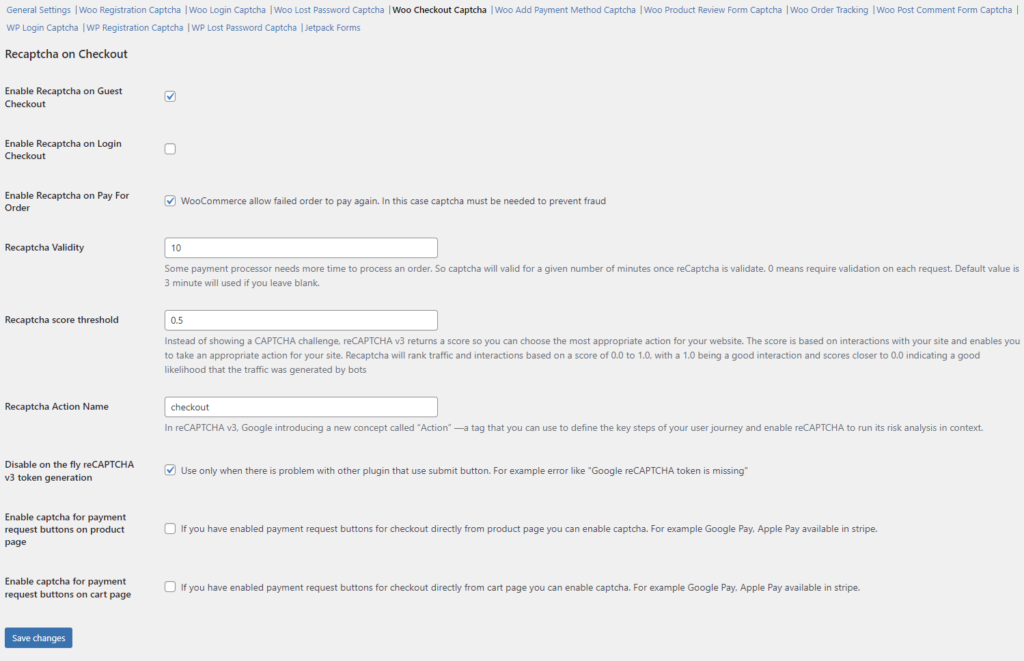
4.5. It also makes sense to enable reCAPTCHA on the Add Payment Method page to prevent card testing attacks.
Please remember that reCAPTCHA may slightly decrease the conversion rate. Use it only if you have a problem with spam orders or see some weird activity in your payment gateway account.
You may find more information about similar tools here: How To Prevent Fraudulent Carding Attacks On Your WooCommerce Store.
Keep your server’s software up-to-date – this is especially important if you manage your server’s software yourself.
How to detect if the store was hacked and how to fix it
The easiest way to detect if your store is compromised or hacked is by using the Wordfence malware scanner.
It’s not perfect, but it can detect most issues. Here is what it looks like if your site has been hacked:
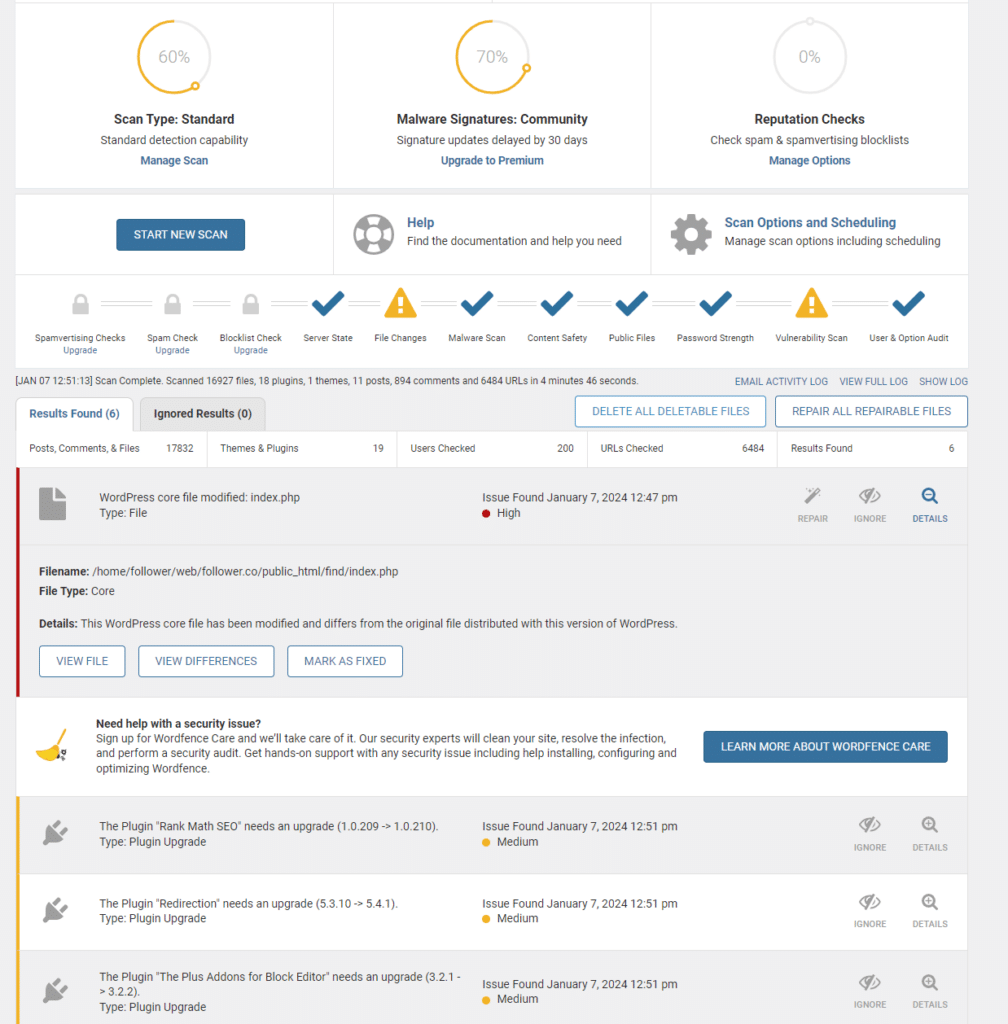
As you may see, the report shows that a WordPress core file has been modified. This is very common on a hacked site.
Let’s click on the View Differences button:
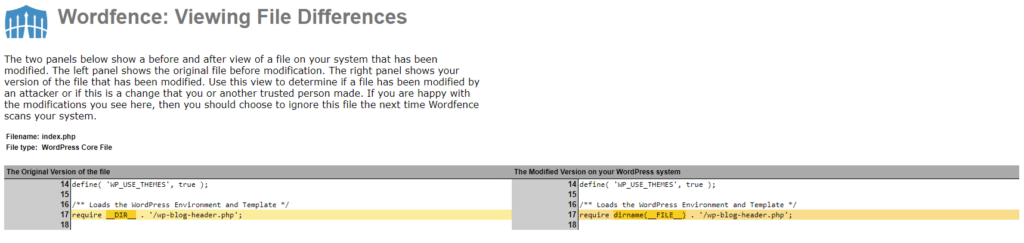
As this is just an example, the file changes are not important. If this was a real example of a compromised site, you would be able to click the Repair button to restore the original and correct version of the file.
If you have out-of-date plugins, you will see a Medium priority alert for each one. Don’t disregard these – remember that out-of-date, insecure plugins are the primary way that WordPress sites are compromised.
Unfortunately, the Wordfence scan does not scan the content of some widgets, posts, and plugin settings. You may need to check these things manually.
For example, if you use a plugin like Custom CSS & JS to add code to the page you will need to manually check those snippets to make sure they have not been corrupted.
Often, malicious code snippets may look like a valid code, but it’s not:
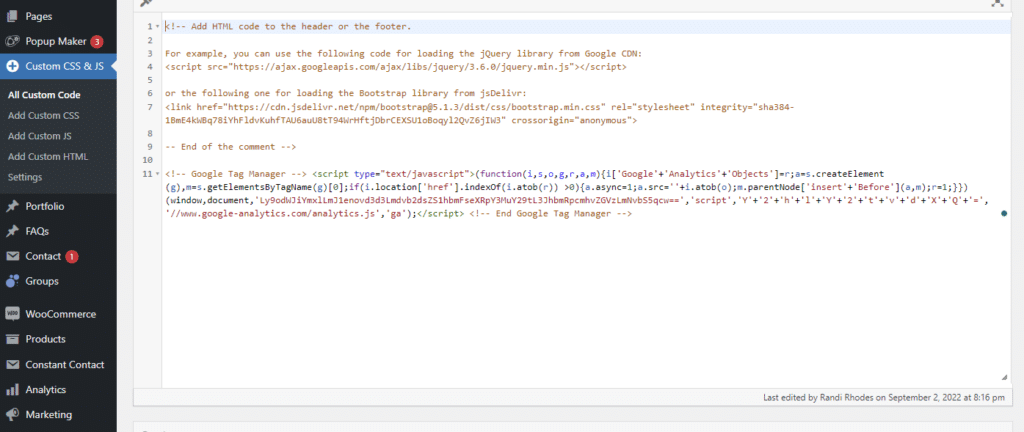
If you find a snippet that is corrupted, you can remove the malicious code, or remove the entire snippet.
As you have no doubt noticed, determining whether a script is safe or not requires some knowledge and expertise. But if you are following our recommendations, the chance that you will have a compromised script is very low.
Keep your site safe
Keeping your WooCommerce site secure is important even if you have a relatively small store.
Wordfence and regular updates offer good enough protection against most attacks.
Has your WooCommerce site been hacked before? How did you resolve it? Share any tips you learned in the comments below.
I hope you’ve learned something!
Follow me on Twitter for more WooCommerce security tips: Andrii Toniievych (@TwistedAndy)
